士欣新聞
資安業者McAfee 公布勒索軟體LockBit的攻擊軌跡-資訊更新
日期:2020-05-25:工程部
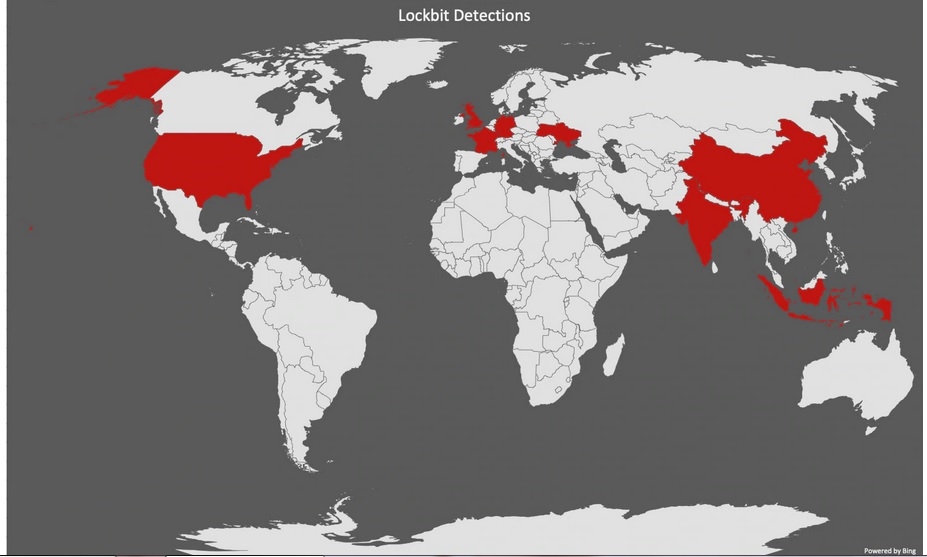
LockBit的攻擊足跡與樣本數並不多,主要是因為它是個非常目標導向的勒索軟體,駭客花了好幾天的時間,暴力破解一個採用過時VPN服務的網頁伺服器,以取得管理員的憑證,接著就在組織內的網路橫行無阻。
有了管理員的權限之後,駭客即透過SMB來偵測內部網路,列出所有可存取的主機,再藉由微軟的遠端存取伺服器(RAS)來存取這些主機,而且不管是在組織內橫向移動,或是部署LockBit都採用了自動化技術。
The Ransomware-as-a-Service (RaaS) hit the threat landscape in September 2019 and was discovered to have breached a company and encrypt the entire network in a few hours. The attacker performed a brute force attack on a web server containing an outdated VPN service. The operation used SMB to perform network reconnaissance and then used the internal Microsoft Remote Access Server to gain access to remote systems. Lockbit attempts to stop multiple services including those belonging to anti-virus, databases, webservers, and other applications.
https://www.mcafee.com/enterprise/en-us/downloads/free-tools/ransomware-decryption.html
解密工具: https://www.nomoreransom.org/en/index.html
https://www.mcafee.com/enterprise/en-us/security-awareness/ransomware.html
相關連結:https://www.mcafee.com/blogs/other-blogs/mcafee-labs/tales-from-the-trenches-a-lockbit-ransomware-story/